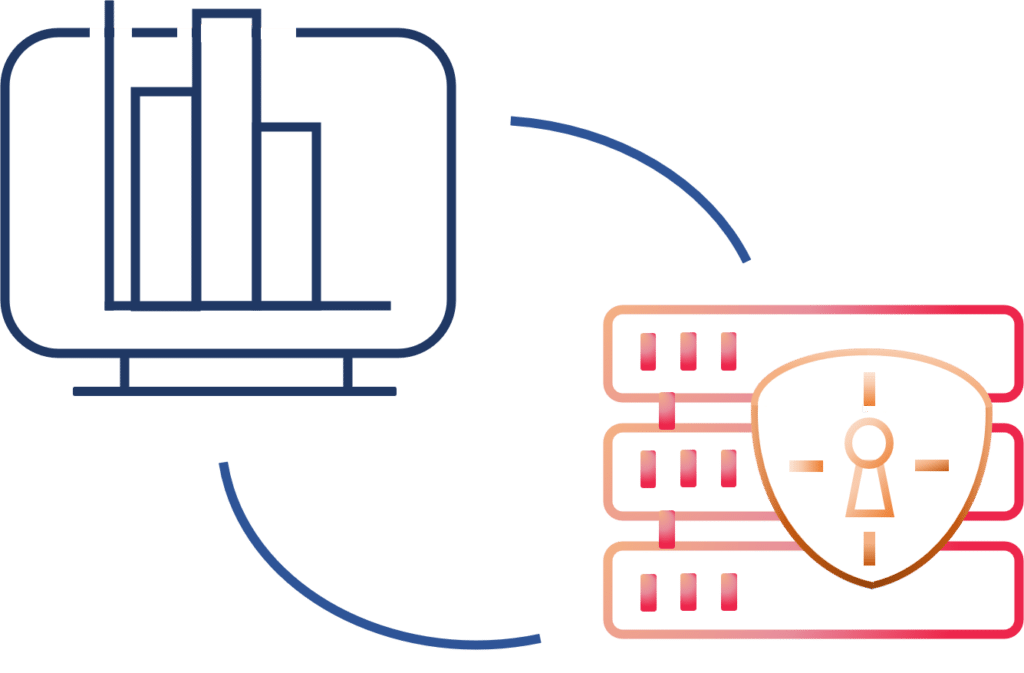
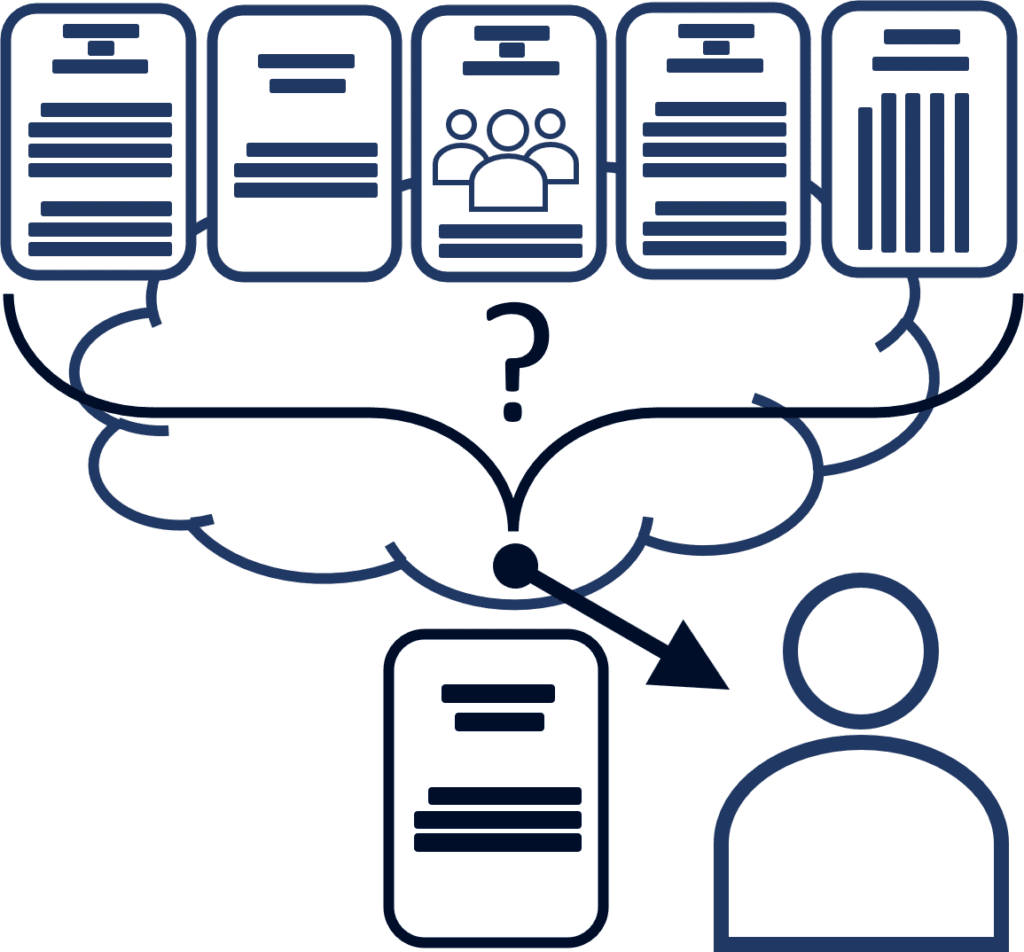
Cryptography Theory and Implementation
Together with our consultants, the Stealth team has led research efforts in a number of the subfields of cryptography that are most relevant in today’s digital age, including: Secure Multi-Party Computation (MPC), Searchable Encryption, Fully Homomorphic Encryption (FHE), Oblivious RAM (ORAM), Private Information Retrieval (PIR), Function Secret Sharing (FSS), Distributed Protocols/Blockchain, Zero-Knowledge Proofs (ZK), and many others. With hundreds of peer-reviewed publications at top-tier venues, we pride ourselves in basing our technologies on rigorous scientific cornerstones.
Our research in these areas includes not only theoretical advancements, but also proof-of-concept software prototypes that demonstrate the feasibility of developing software based on (formally evaluated) cryptographic primitives that enjoy the strongest level of protection against insider and outsider attacks. As part of numerous funded programs through the Department of Defense and beyond, we have matured our technologies, demonstrated them in the laboratory, integrated them with academic and industry collaborators, and stress-tested them in both scientific and military exercises. All of this aligns with our key vision: unlocking the power of data while keeping it safe and secure, from business intelligence to battlefield intelligence, from individual privacy to institutional privacy.
Advancing the state-of-the-art for PETs through R&D
In the nearly two decades since the formation of Stealth, plus the decades of work by our team members before this, we have a wealth of R&D experience to draw upon, and we continue to push forward the field of cryptography and the development of secure and efficient privacy-preserving software. While most of our funding comes from projects for the government and non-profit organizations, we are able to disseminate our work to a broad audience of security-minded researchers and practitioners in several ways:
- Presenting R&D advancements at conferences, workshops, and industry days (visit our Newsroom);
- Publishing research in leading journals and conferences;
- Developing open-source code for software prototypes and various PET libraries, including:
- Zero-Knowledge Tools:
- EMP Toolkit: backend prover-verifier functionality
- Wizkit: tools for reading and writing ZK statements
- Computing on Encrypted Data:
- SAFRN: aggregate statistics across numerous users’ private data
- PULSAR: various MPC tools, including finding central meeting locations privately
- Cryptographic Primitives Libraries:
- pfss: Function Secret Sharing (FSS) library
- tumbolandia: Homomorphic Secret Sharing (HSS) library
- sst: Basic cryptographic primitives (large numbers, hash, encryption, etc.)
- Zero-Knowledge Tools:
Building custom solutions that emphasize feasibility and performance.
While our Stealth team has made a substantial impact on the field of theoretical cryptography, our passion lies in bringing these theoretical primitives to bear in real-world applications. This includes redesigning protocols for optimization, making adjustments for resource-constrained environments, adjusting the model based on actual threat scenarios or system requirements, and finally developing software prototypes to demonstrate viability and provide empirical evidence of the theoretical performance claims.
For instance, Know-Your-Customer (KYC) procedures are important for anything from finance to sales and advertising. Analytics in this area are becoming ever more data-hungry and require sources of information that may be protected or siloed away. By applying the types of secure computing that our Stealth team are experts in, organizations can reduce the friction in computing on sensitive sources of data, enabling linking, aggregating, and finding insights about data while keeping them private.